Secure Cloud Sharing
File-level encrypted security across cloud storage and sharing
350%
Increase in file-sharing
phishing attacks
82%
of data breaches involved data stored in the cloud
83%
of businesses don't encrypt of the sensitive data they store in the cloud
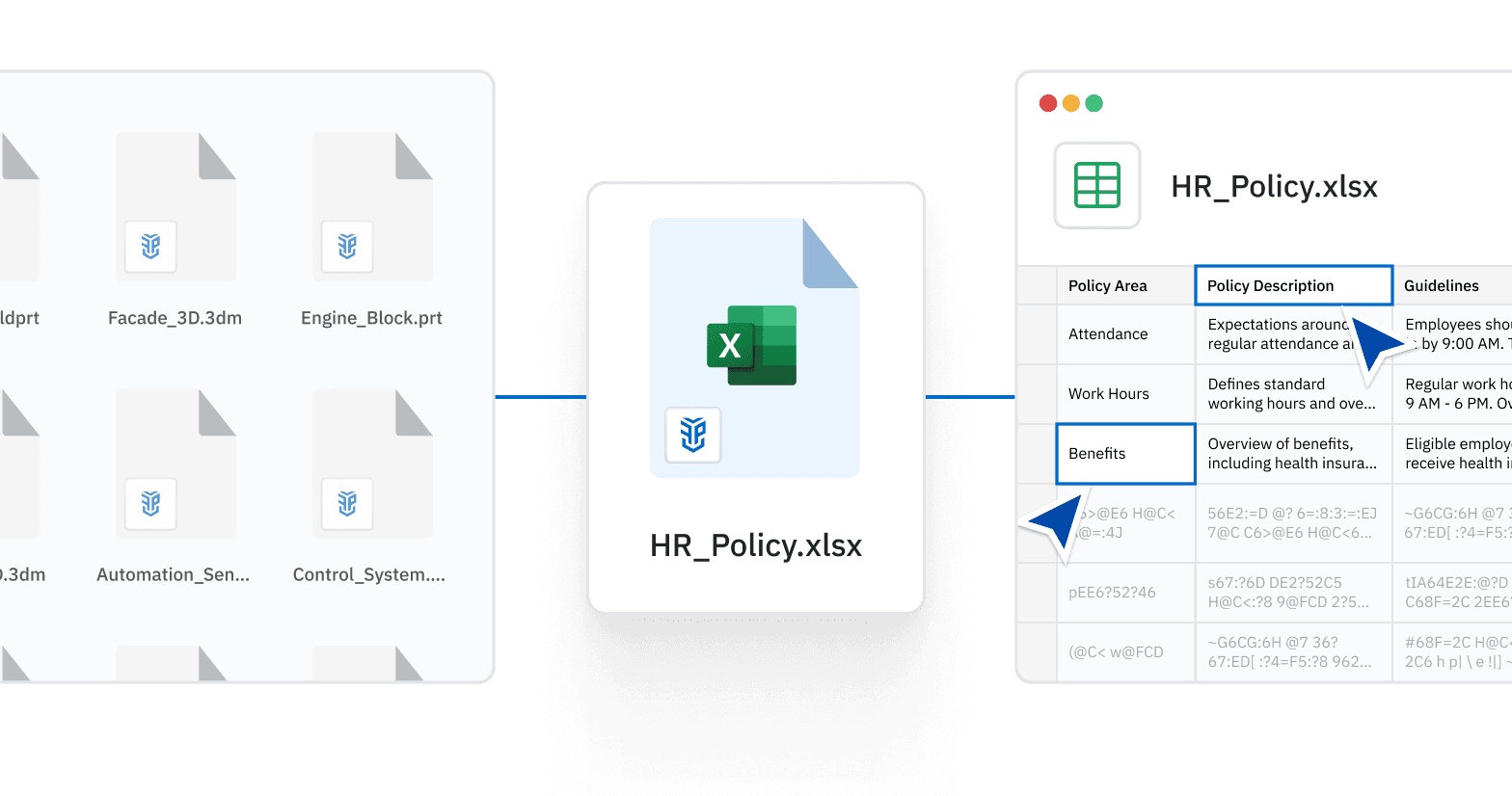
Overcome the Challenges
of Secure File Sharing
Foster collaboration without jeopardizing data security, enhance productivity by maintaining
current workflows, and ensure the integrity and security of sensitive data.
Enhanced Data Protection: At rest, in transit, and in use
Granular Access Controls
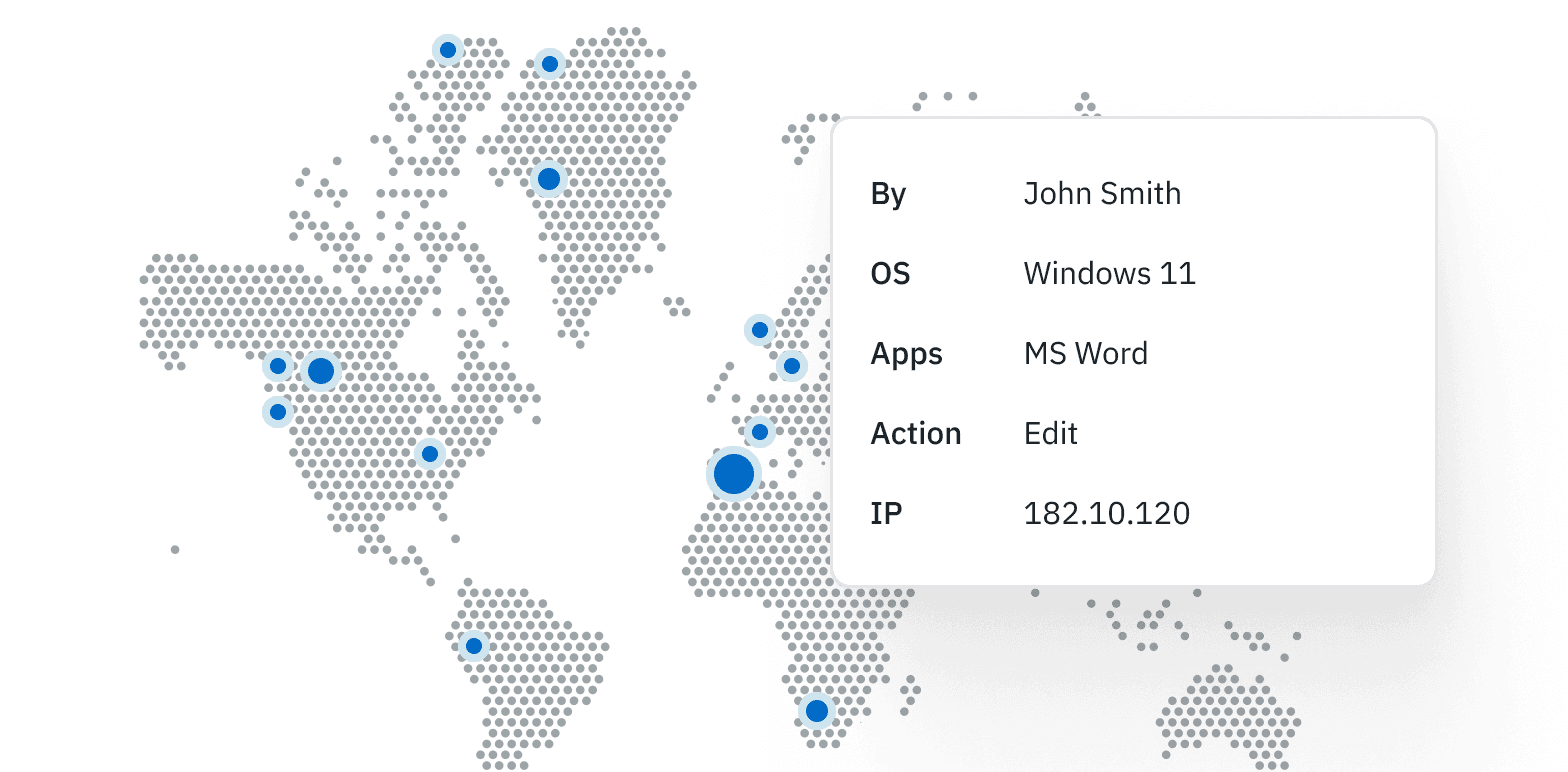
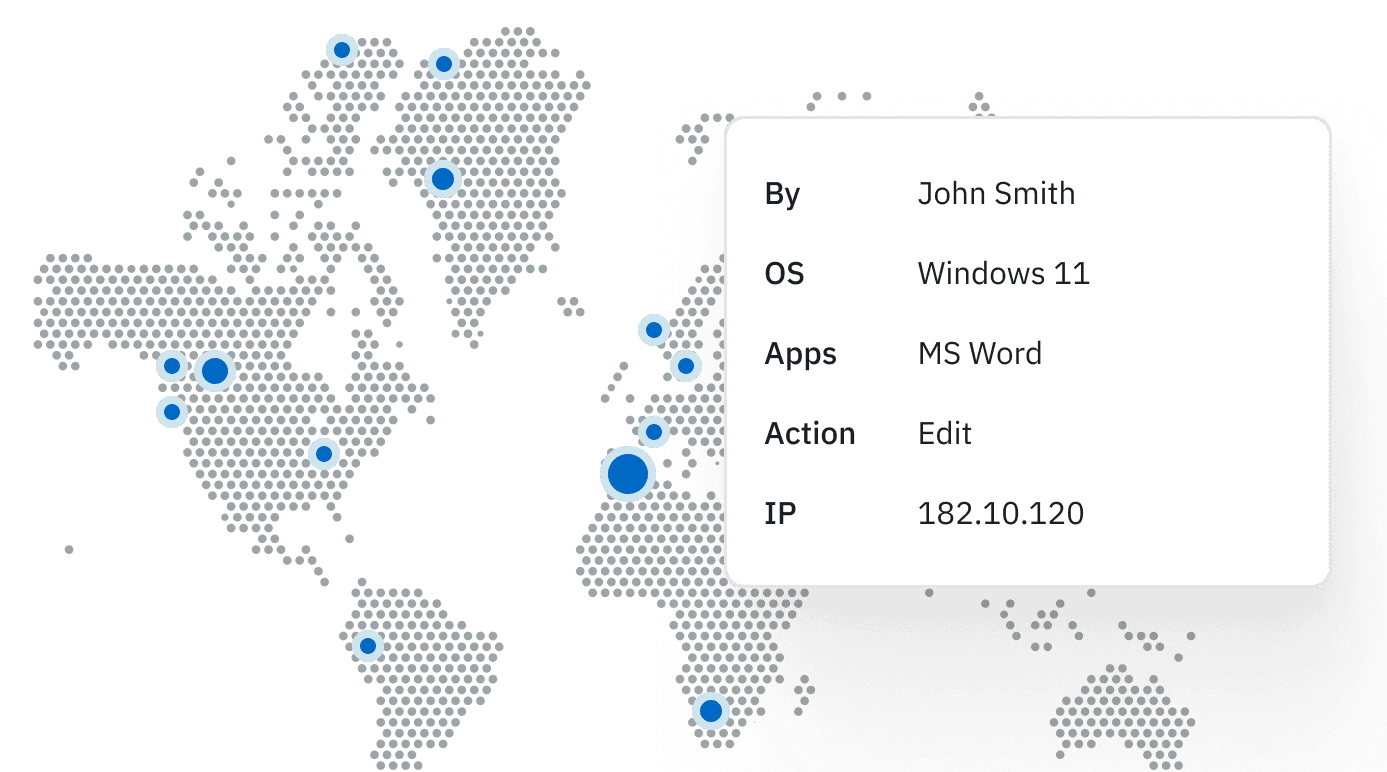
Auditing and Monitoring on Every File
FenixPyre provides robust auditing and monitoring capabilities, allowing organizations to track file access and activity in real time. FenixPyre visibility enables proactive detection of suspicious behavior and helps organizations maintain compliance with regulatory requirements.
Comprehensive Compliance Support
FenixPyre's secure EFSS solution assists organizations in meeting regulatory compliance requirements, such as CMMC, GDPR, HIPAA, PCI, and other NIST-based regulatory frameworks that require encryption, access control, and monitoring. By implementing stringent security measures and offering compliance reporting tools, FenixPyre helps organizations demonstrate adherence to relevant regulations.
User-Friendly Collaboration
Frictionless Secure File Sharing
Despite stringent security measures, FenixPyre ensures that collaboration remains seamless and user-friendly. Users can securely share files internally and externally, with features like secure links, password protection, and expiration dates to control access and mitigate security risks. FenixPyre keeps files encrypted not just at rest and in transit, but also when they are in use. As a result, control is always retained, even during external collaboration.
Productivity Enhancement
Organizations look for ways to enhance productivity via the use of AI-based content creation and enhancement tools. However, the major concern is the lack of privacy and the loss of control of sensitive content. By making security directly baked into data, FenixPyre takes away the security concerns and provides a simple platform to reap the value of collaborative AI, without compromising the security of data.
Integration with Existing Systems
FenixPyre seamlessly integrates with existing enterprise systems and identity management solutions, streamlining user authentication and access control processes. This ensures that organizations can leverage their existing infrastructure while enhancing data security.
Sharing Policies Automated
Least privilege access control, and logging. Delivered transparent to users, integrated into their existing workflows, easy collaboration with external parties.