Data Governance
Data Governance
Data Governance
Innovative
Solution to Ensure Compliance with Rules and Policies
Easy adherence to data governance and
compliance with file-level encryption.

Protecting data is
the cornerstone of governance and compliance
Protecting data is the cornerstone of governance and compliance
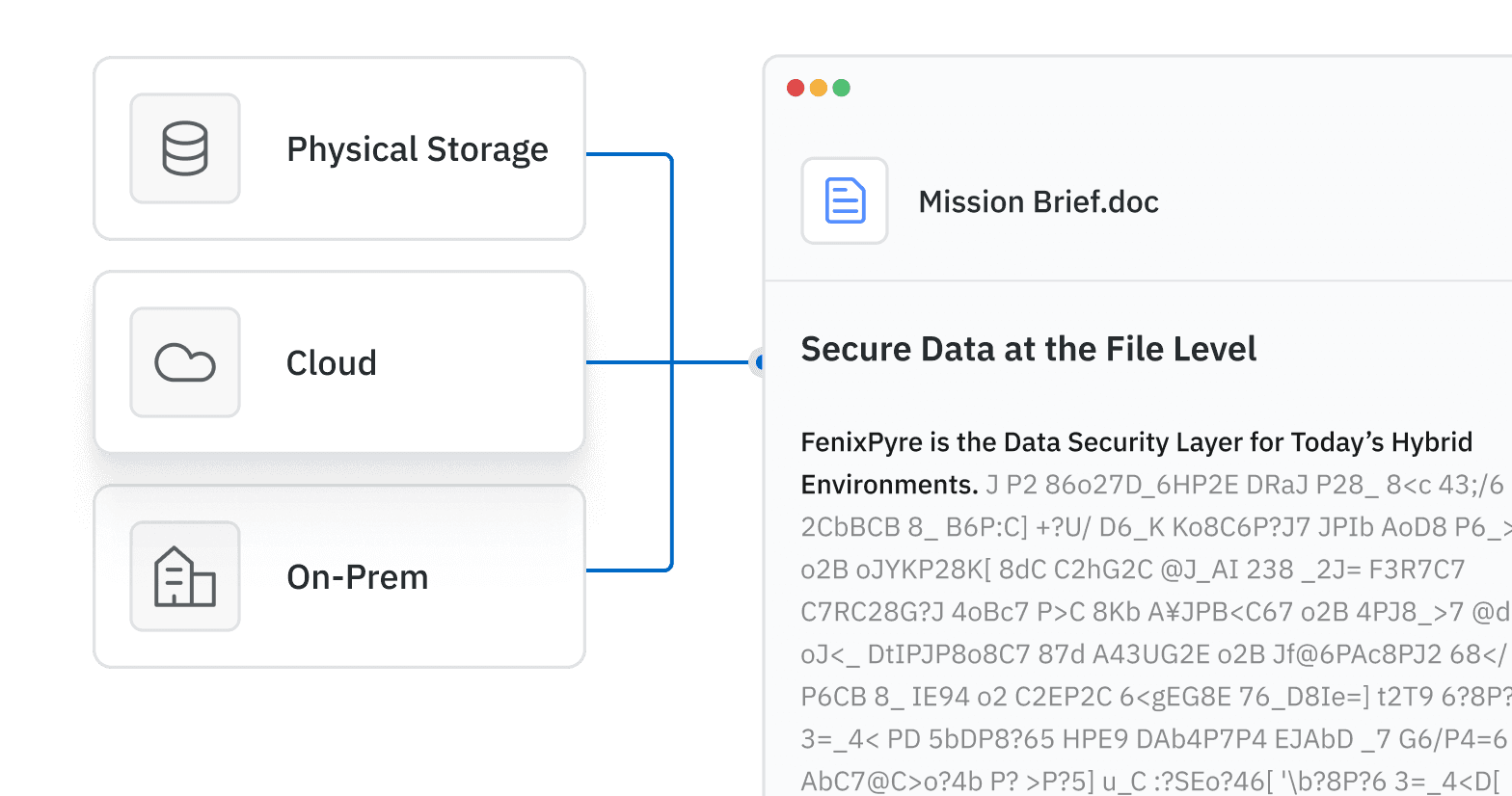
Managing your data effectively is key to staying secure and compliant, and encryption plays a critical role. With the right data governance software, like FenixPyre, you can easily take control of your data and maintain privacy, access, and integrity. At FenixPyre, we make data governance simple and stress-free, ensuring your data stays protected and compliant, no matter where it travels.
Managing your data effectively is key to staying secure and compliant, and encryption plays a critical role. With the right data governance software, like FenixPyre, you can easily take control of your data and maintain privacy, access, and integrity. At FenixPyre, we make data governance simple and stress-free, ensuring your data stays protected and compliant, no matter where it travels.







Your Data Stays Protected!
FIPS encryption ensures that even in a breach, stolen files remain secure and inaccessible.







Your Data Stays Protected!
FIPS encryption ensures that even in a breach, stolen files remain secure and inaccessible.







Your Data Stays Protected!
FIPS encryption ensures that even in a breach, stolen files remain secure and inaccessible.
70%
of service organizations must comply with six security and privacy frameworks.
30%
of compliance officers are implementing a ‘demonstrably compliant culture
$265 billion
of risk and compliance professionals say automating processes would reduce complexity and costs
See FenixPyre Ransomware Protection in Action
See FenixPyre Ransomware Protection in Action
See FenixPyre Ransomware Protection in Action
Regulatory Compliance for Data Protection: Delivered
From GDPR to HIPAA, CMMC, to GLBA, and more, data governance and encryption are critical to protect sensitive data. FenixPyre solves data governance by making data self-protecting, regardless of its location, at rest, in transit, and even in use.
From GDPR to HIPAA, CMMC, to GLBA, and more, data governance and encryption are critical to protect sensitive data. FenixPyre solves data governance by making data self-protecting, regardless of its location, at rest, in transit, and even in use.


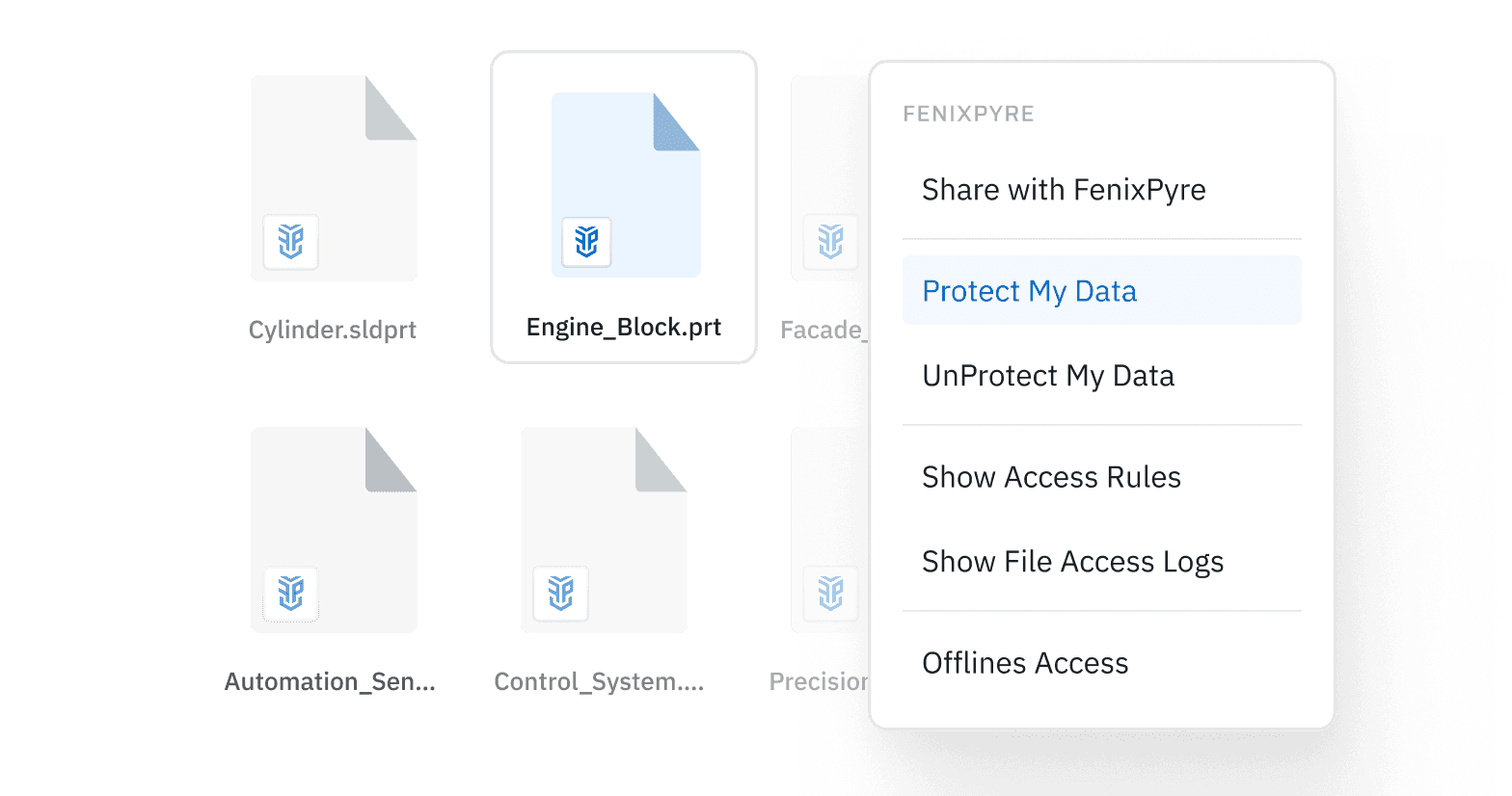
Policy Adherence: Effortless
People often create workarounds when security and compliance processes and technologies are perceived to ‘impede’ efficiency. FenixPyre’s solution eliminates this issue, by providing a frictionless and invisible solution with no user burden or change in workflow.
People often create workarounds when security and compliance processes and technologies are perceived to ‘impede’ efficiency. FenixPyre’s solution eliminates this issue, by providing a frictionless and invisible solution with no user burden or change in workflow.


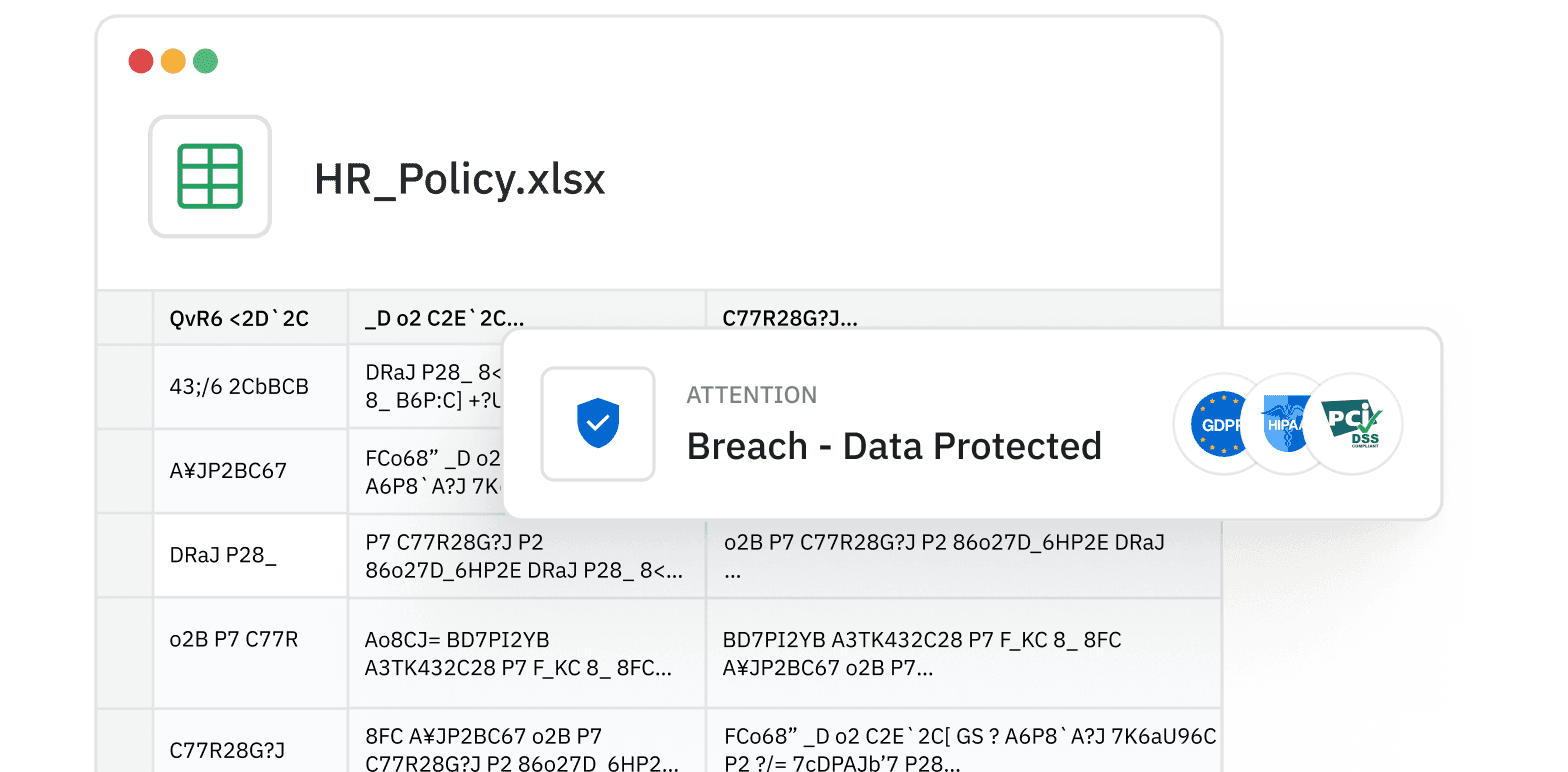
Data Privacy: Ensured
Safeguard sensitive information responsibly and in compliance with laws and regulations. FenixPyre’s patented encryption ensures data privacy wherever the file travels – in use, transit, and at rest – and is unreadable if breached.
Safeguard sensitive information responsibly and in compliance with laws and regulations. FenixPyre’s patented encryption ensures data privacy wherever the file travels – in use, transit, and at rest – and is unreadable if breached.


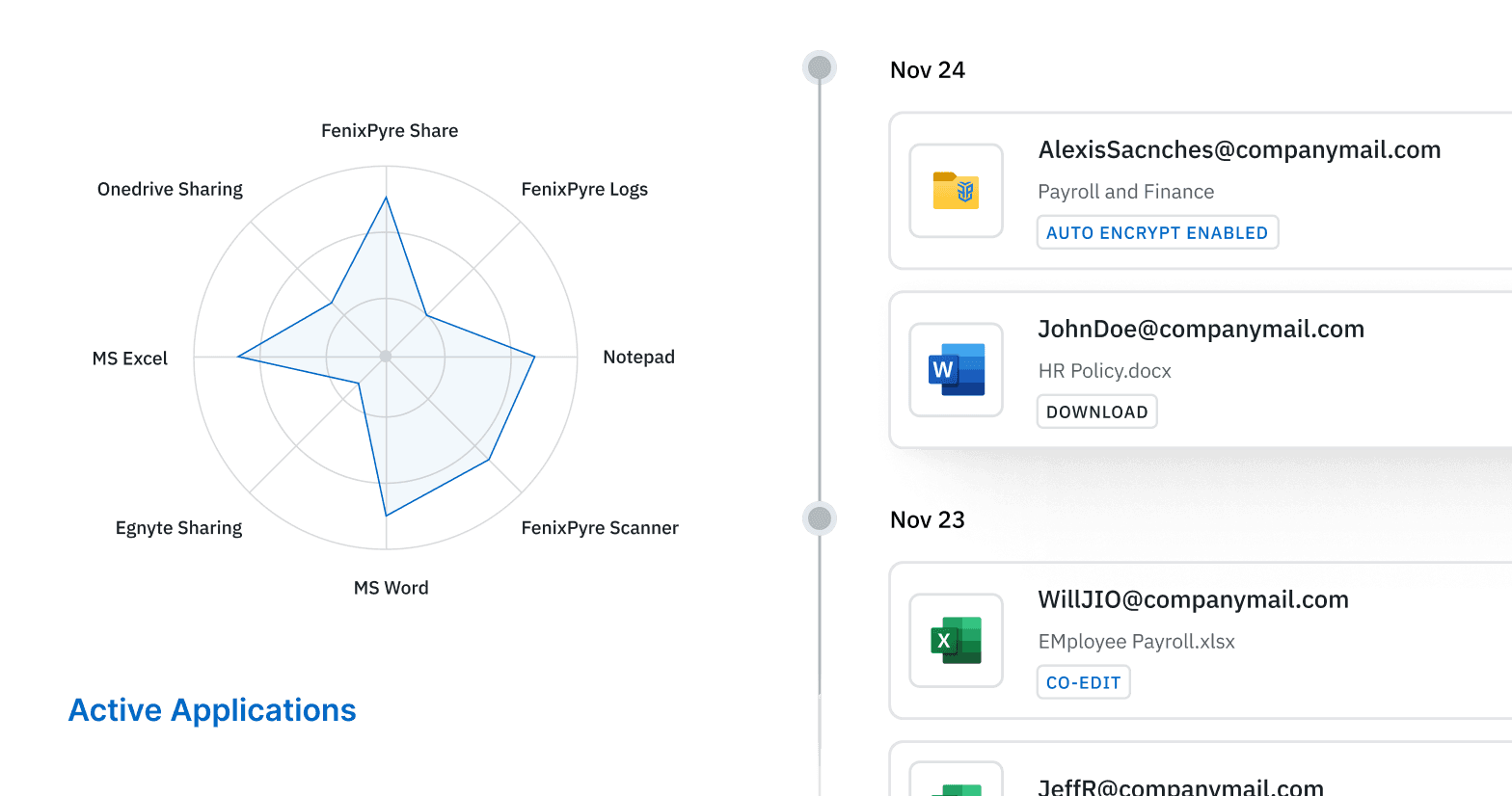
Audit and Traceability: Built-in
With FenixPyre, every file carries compliance with it, maintaining detailed audit trails. You’ll know who accessed data, how and when; a key requirement for regulatory and compliance reporting purposes.
With FenixPyre, every file carries compliance with it, maintaining detailed audit trails. You’ll know who accessed data, how and when; a key requirement for regulatory and compliance reporting purposes.


FenixPyre
FenixPyre
FenixPyre
The ‘Easy Button’ for
Data Governance & Compliance
It’s difficult to enforce policies across the organization, especially
as workers are remote, on personal devices, or sharing or storing sensitive data.
File-level
Encryption
FenixPyre employs zero-trust principles - the data is self-protecting, eliminating reliance on perimeter defenses often breached in ransomware attacks.
FenixPyre employs zero-trust principles - the data is self-protecting, eliminating reliance on perimeter defenses often breached in ransomware attacks.
Access
Control
Access Control
Data is encrypted at rest, in transit, and in use. Persistent encryption ensures ransomware attacks cannot exploit data.
Data is encrypted at rest, in transit, and in use. Persistent encryption ensures ransomware attacks cannot exploit data.
Integration with Existing Systems
The encryption and decryption processes are automatic and transparent, removing the need for user involvement.
Zero-Trust
Architecture
Zero-Trust Architecture
FenixPyre protects data at the file level, eliminating the reliance on perimeter security, simplifying compliance, and reducing risks of data breaches.
FenixPyre protects data at the file level, eliminating the reliance on perimeter security, simplifying compliance, and reducing risks of data breaches.
FenixPyre protects data at the file level, eliminating the reliance on perimeter security, simplifying compliance, and reducing risks of data breaches.
Data Governance FAQs
How does encryption support data governance?
How does encryption support data governance?
How does encryption support data governance?
What types of data should be encrypted for compliance?
What types of data should be encrypted for compliance?
What types of data should be encrypted for compliance?
How does encryption help with data classification?
How does encryption help with data classification?
How does encryption help with data classification?
What are the benefits of encryption for data loss prevention?
What are the benefits of encryption for data loss prevention?
What are the benefits of encryption for data loss prevention?
How does encryption enhance data access controls?yption capabilities should organizations look for?
How does encryption enhance data access controls?yption capabilities should organizations look for?
How does encryption enhance data access controls?yption capabilities should organizations look for?
What encryption capabilities should organizations look for?
What encryption capabilities should organizations look for?
What encryption capabilities should organizations look for?

solutions

© 2018-2025 FenixPyre Inc, All rights reserved

solutions
7775 Walton Parkway
Suite 224
New Albany, OH 43054

© 2018-2025 FenixPyre Inc, All rights reserved

solutions
7775 Walton Parkway
Suite 224
New Albany, OH 43054

© 2018-2025 FenixPyre Inc, All rights reserved

