Without disrupting your business processes and digital workflows
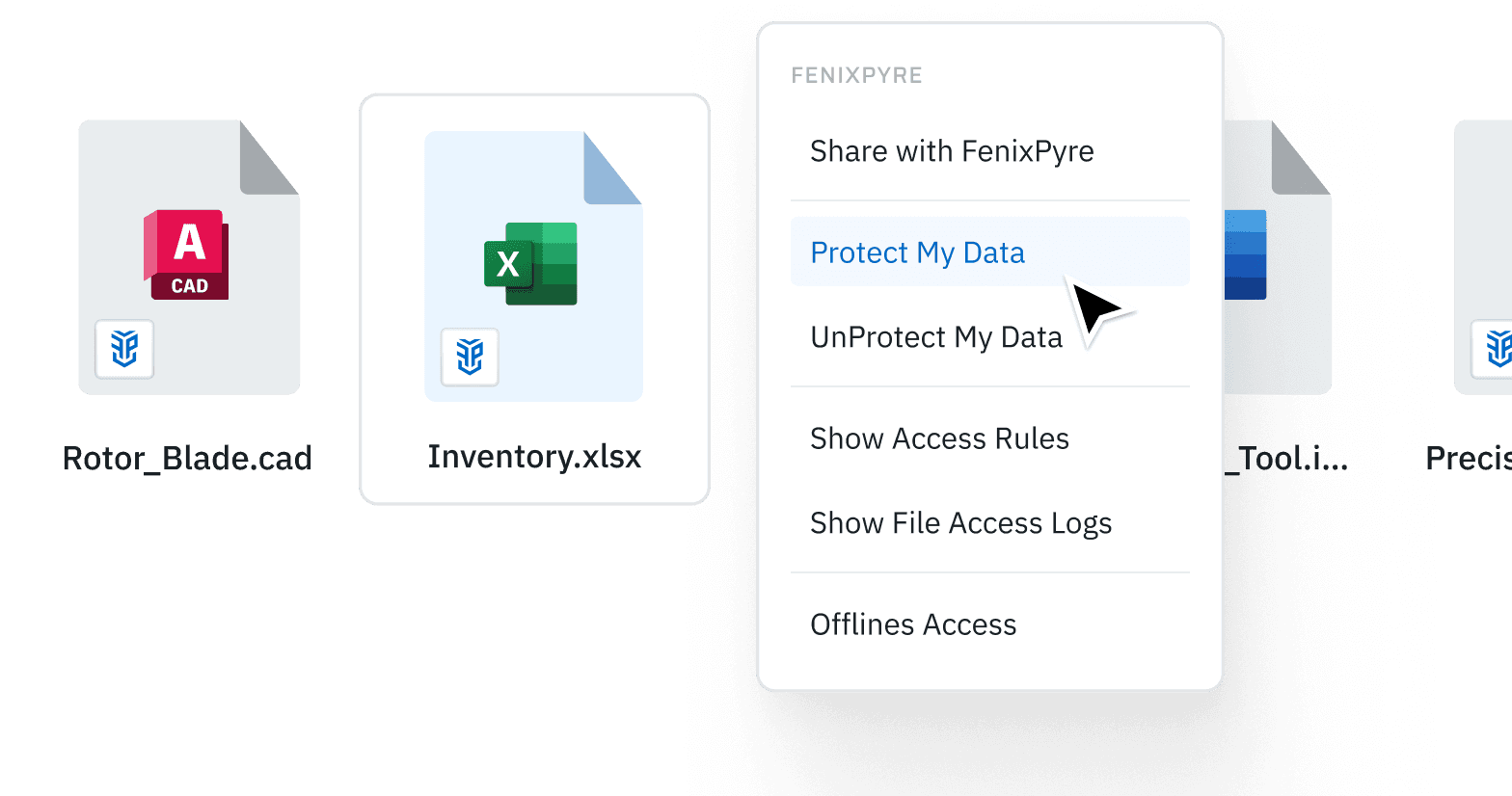
FenixPyre secures all file types and applications—from CAD designs to documents—without changing your workflows. Whatever the format or system, your CUI stays encrypted and protected, at rest, in transit and in use.
FIPS 140-2 Validated Cryptographic Modules
Your files are protected at rest, in transit, and at point of use in accordance with NIST and DFARS requirements for end-to-end encryption of CUI. You control the primary encryption keys.
Deploy in Under 2 hrs.
Reduce CMMC Compliance Effort
End-to-end encrypted files means only authorized users and devices can access files secured by FenixPyre. All unauthorized devices are not categorized as CMMC CUI Assets, because they cannot decrypt the files.
Streamline Incident Response
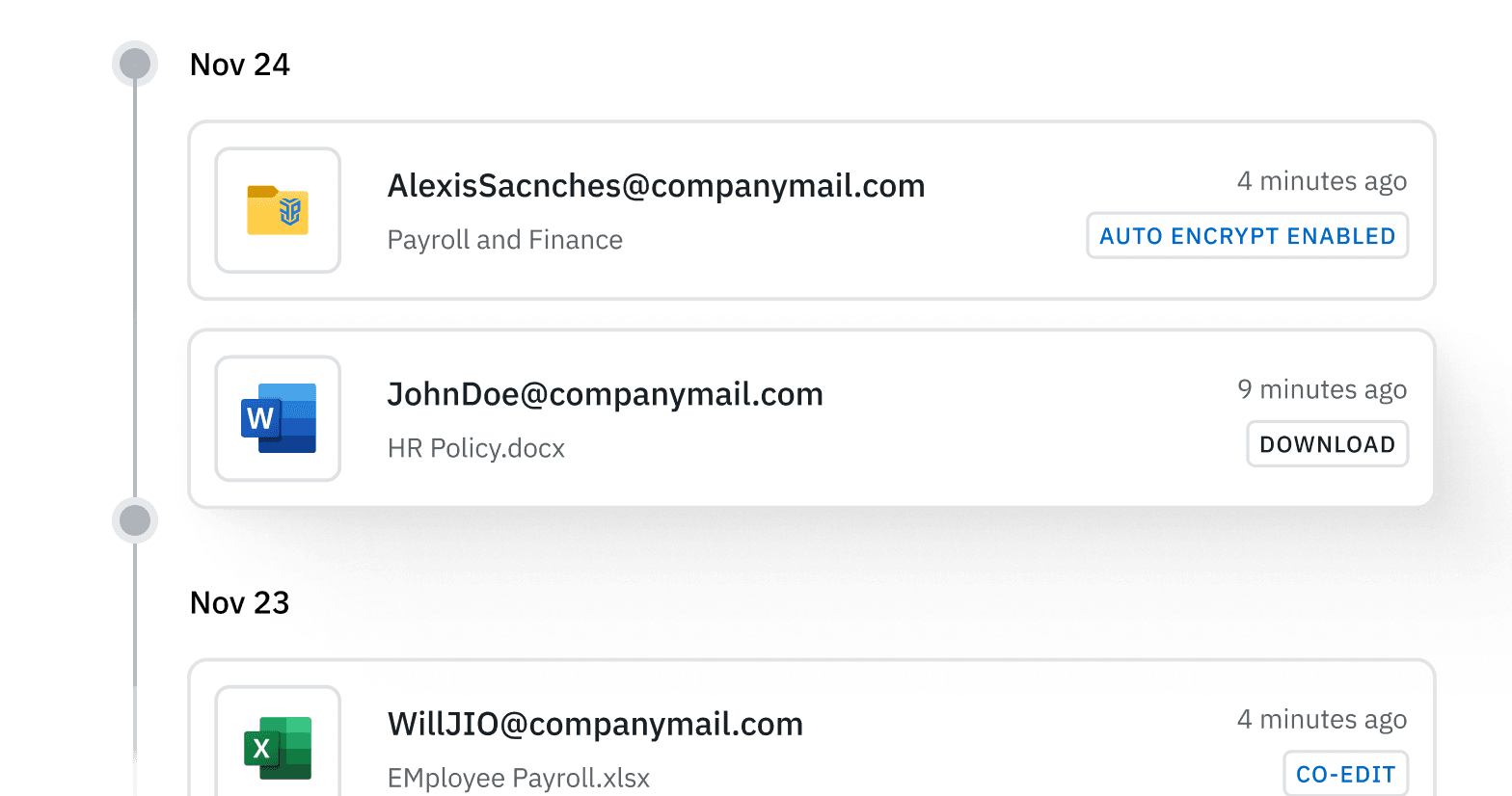
FenixPyre audits all access attempts from anywhere. With the click of a button, you can meet the DFARS 7012 72-hour requirement for reporting the breach scope to DIBNet.