Data Security
Platform
Get on the fast track to
end-to-end data protection
FenixPyre’s revolutionary platform ensures your sensitive and CUI files are inherently
secure at all times without disrupting your day-to-day business.
Fast and easy
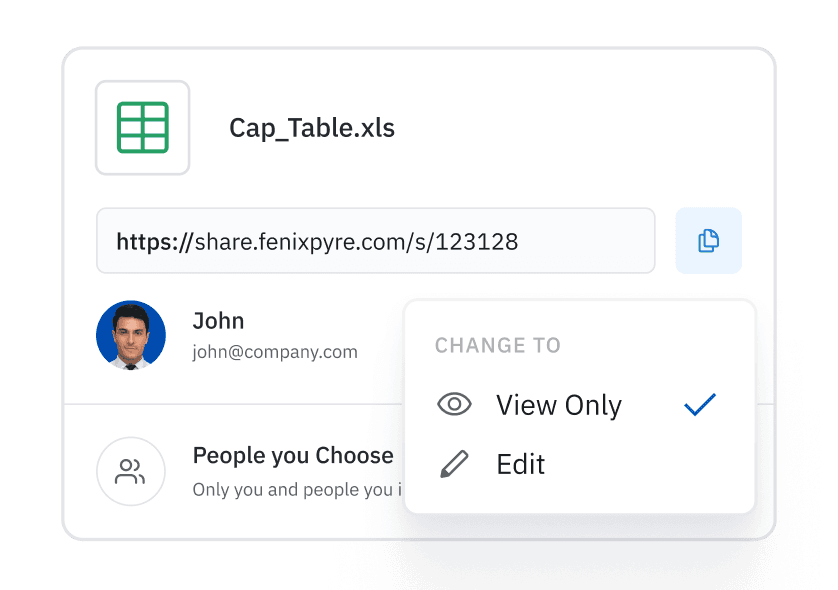
Deploys in under an hour. Access rights can easily be managed by business owners.
Frictionless fit
Fits into your existing workflows and processes, not the other way around.
IT Ease
Unparalleled versatility
For Department of Defense (DOD) contractors and subcontractors, CMMC adherence is timely and has significant business implications if miss the deadlines. FenixPyre helps achieve CMMC compliance without changing the way you operate or disrupting your business. Since FenixPyre utilizes current workflows and processes, it eliminates data migration to costly enclaves or government cloud services and reduces your time to compliance. If you’re already working with a service partner, we can help speed up the process.
Traditional Data Loss Prevention approaches have failed to eliminate data losse completely. FenixPyre inverts the equation with a unified rules and policy engine that works on-premises and across multi-cloud environments to make data theft irrelevant by applying zero trust to the files themselves. FenixPyre’s data security platform is differentiated by its ability to keep files encrypted both in use and accessed outside the organization in collaboration mode. As a result, files remain protected even if they are exfiltrated. FenixPyre can sit alongside existing DLP infrastructure and serve as the final layer of protection, or it can replace it entirely.
With FenixPyre, data is self–protecting and becomes its own perimeter. Each file is individually FIPS-validated encrypted at rest, in transit, and even while in using (AES) 256-bit military-grade encryption.
Patented heartbeat technology constantly verifies access rules in real-time based on a myriad of data sources. When an access rule is broken, FenixPyre instantly revokes access, even when the file is in use.
Digital Chain of Custody via Forensic Logging
Sensitive data is tracked in real time, with audit trails of each request, including physical location creating atrue chain of custody for digital data.
Trusted across
industries