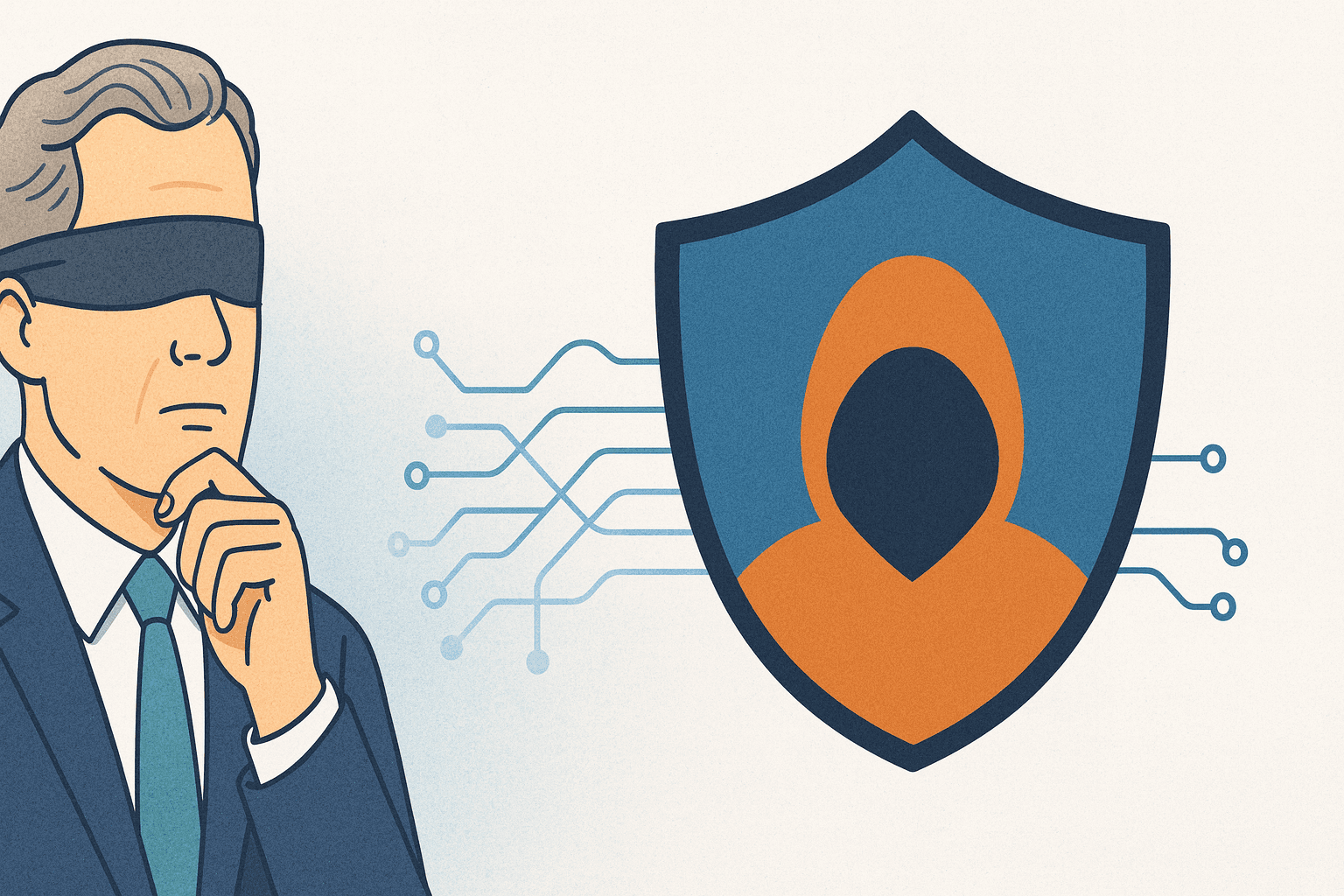
We Ensure your Data Cannot Be Stolen Even with Valid Credentials
We Ensure your Data
Cannot Be Stolen
Even with Valid Credentials
File-Centric Security Platform
File-Centric Security Platform
File-Centric Security Platform
File-Centric Security begins by protecting the obvious – the files
FenixPyre’s revolutionary platform ensures your sensitive files and CUI are inherently secure at all times without disrupting your day-to-day business.



File-Centric Security
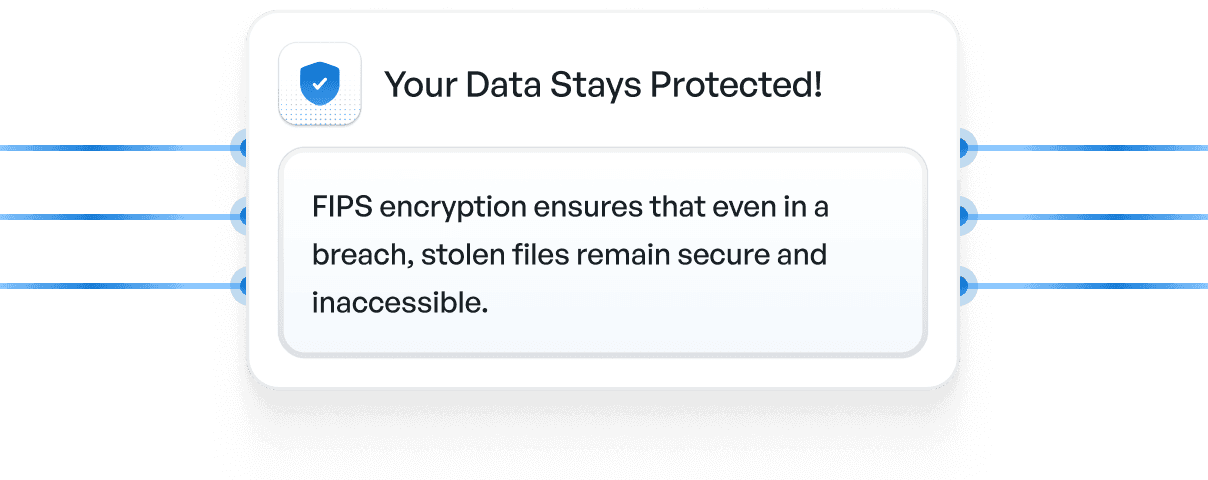
Disk encryption (at rest), TLS (in transit) most companies have but this isn’t enough to secure your files once a bad actor is inside your network or under a man in the middle attack. FenixPyre's encrypts the sensitive files you choose so network access to the files doesn’t lead to a data breach. Secured with AES-256 encryption and FIPS 140-2 validated modules.
Disk encryption (at rest), TLS (in transit) most companies have but this isn’t enough to secure your files once a bad actor is inside your network or under a man in the middle attack. FenixPyre's encrypts the sensitive files you choose so network access to the files doesn’t lead to a data breach. Secured with AES-256 encryption and FIPS 140-2 validated modules.



Seamless User Experience
Open, save, and edit documents without any change to your current user experience. FenixPyre's file-centric security is able to end the annoyance of false positives or blocking users from accessing and sharing content caused by DLP solutions. Our file-centric security occurs automatically and seamlessly, ensuring a frictionless experience while enforcing security and compliance.
Open, save, and edit documents without any change to your current user experience. FenixPyre's file-centric security is able to end the annoyance of false positives or blocking users from accessing and sharing content caused by DLP solutions. Our file-centric security occurs automatically and seamlessly, ensuring a frictionless experience while enforcing security and compliance.



Secure Any File Type
FenixPyre encrypts any file type and secures any application, from Microsoft Office to advanced CAD tools like Revit and SolidWorks. It integrates seamlessly into your workflows, ensuring security without disruption. Users can collaborate freely, knowing their data remains protected without changing how they work.
FenixPyre encrypts any file type and secures any application, from Microsoft Office to advanced CAD tools like Revit and SolidWorks. It integrates seamlessly into your workflows, ensuring security without disruption. Users can collaborate freely, knowing their data remains protected without changing how they work.
FenixPyre encrypts any file type and secures any application, from Microsoft Office to advanced CAD tools like Revit and SolidWorks. It integrates seamlessly into your workflows, ensuring security without disruption. Users can collaborate freely, knowing their data remains protected without changing how they work.



Use Your Existing File Stores
Users don’t need to leave the location where sensitive data is typically created and stored. They can continue to work in the locations they are used to. FenixPyre adds a robust security layer to files in your existing on-prem and cloud storage platforms, including Network Shares and SharePoint, OneDrive, Box, Egnyte.


Seamless Integration with Existing IT Stack
FenixPyre effortlessly works with your existing technology stack, including IAM solutions like Entra ID and Okta, HSMs like Azure and Google HSM, and SIEM tools like Splunk and Datadog. It ensures smooth integration, enhancing your security ecosystem without added complexity.


Integrate with Existing File Stores
Users don’t need to leave the location where sensitive data is typically created and stored. They can continue to work in the locations they are used to. FenixPyre adds a robust security layer to files in your existing on-prem and cloud storage platforms, including Network Shares and SharePoint, OneDrive, Box, Egnyte.


Seamless Integration with Existing IT Stack
FenixPyre effortlessly works with your existing technology stack, including IAM solutions like Entra ID and Okta, HSMs like Azure and Google HSM, and SIEM tools like Splunk and Datadog. It ensures smooth integration, enhancing your security ecosystem without added complexity.
Implementing FenixPyre in Three Steps
FenixPyre integrates with your existing IT stack and complements your current security architecture.
Choose what you want to protect

Any Folder, on-prem or on the cloud

Any File Type, simple docs or complex CAD designs

Any Application, only approve the applications you want
Pick who get access

Connect your Identity Provider

Setup User Policies

Assign Users to Policies
Protect your files and get started

Encrypt files at scale

Deploy FenixPyre clients

Simply Double click on files
Choose what you want to protect

Any Folder, on-prem or on the cloud

Any File Type, simple docs or complex CAD designs

Any Application, only approve the applications you want
Pick who get access

Connect your Identity Provider

Setup User Policies

Assign Users to Policies
Protect your files and get started

Encrypt files at scale

Deploy FenixPyre clients

Simply Double click on files
Choose the Folders


Any Folder, on-prem or on the cloud


Any File Type, simple docs or complex CAD designs


Any Application, only approve the applications you want
Pick who get access


Connect your Identity Provider


Setup User Policies


Assign Users to Policies
Protect your files and get started


Encrypt files at scale


Deploy FenixPyre clients


Simply Double click on files

Locate your CUI

Any folder on your on-prem servers

Any File Type, simple docs or complex CAD designs

Any Application, only approve the applications you want

Pick who get access to CUI

Connects with your IAM

Setup User Policies

Assign Users to Policies

Encrypt your CUI

FIPS 140-2 Validated Cryptographic Modules

Deploy FenixPyre on servers and endpoints

Simply Double click on files
use cases
use cases
use cases
The Most comprehensive platform for protecting your sensitive data
CMMC CUI Protection
Gain a simplified remedy to many of the CMMC compliance requirements with a CUl solution that reduces certification time and fits with your existing business processes.


CMMC CUI Protection
Gain a simplified remedy to many of the CMMC compliance requirements with a CUl solution that reduces certification time and fits with your existing business processes.


TPRM & Secure File Sharing
Securely share sensitive files for collaboration and compliance. Make uncontrolled data flow across diverse locations, including cloud sharing, a non-issue.
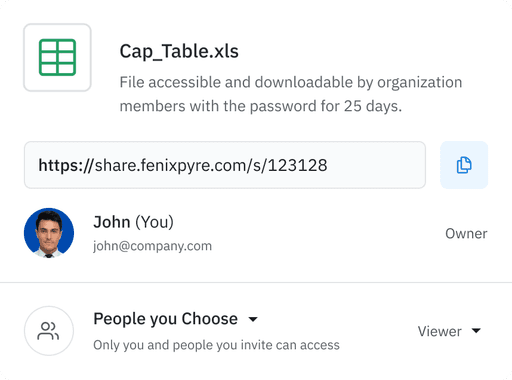
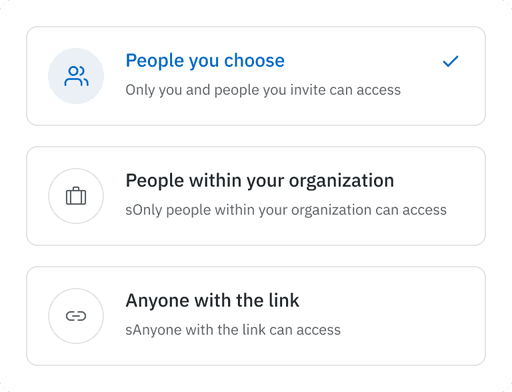
TPRM & Secure File Sharing
Securely share sensitive files for collaboration and compliance. Make uncontrolled data flow across diverse locations, including cloud sharing, a non-issue.


Insider Threat Protection
Employees come and go, make sure your data doesn’t go with them. FenixPyre keeps terminated and exiting employees from taking sensitive and proprietary data with them when they leave.


Insider Threat Protection
Employees come and go, make sure your data doesn’t go with them. FenixPyre keeps terminated and exiting employees from taking sensitive and proprietary data with them when they leave.


Ransomware Protection
Make Ransomware threats a thing of the past with self-protecting data security management that ensures data is always protected and useless cybercriminals if exfiltrated.


Ransomware Protection
Make Ransomware threats a thing of the past with self-protecting data security management that ensures data is always protected and useless cybercriminals if exfiltrated.


Data Governance
Ensure sensitive information remains protected based on factors such as user identity, location, and device and is tracked for every file with patented, context-aware encryption

Daniel K wants to access your file.
LOCATION
New York, USA
DEVICES
Apple iPhone 14
Data Governance
Ensure sensitive information remains protected based on factors such as user identity, location, and device and is tracked for every file with patented, context-aware encryption

Daniel K wants to access your file.
LOCATION
New York, USA
DEVICES
Apple iPhone 14
Trusted across industries















Featured On The Blog
Secure, out of the box

Zero trust security
at the core
FenixPyre’s File-Centric Security Platform brings micro-perimeters to the file. With FenixPyre, every file has its own independent security perimeter, and every request to use it is verified.

Zero trust security
at the core
FenixPyre’s File-Centric Security Platform brings micro-perimeters to the file. With FenixPyre, every file has its own independent security perimeter, and every request to use it is verified.

Zero trust security
at the core
FenixPyre’s File-Centric Security Platform brings micro-perimeters to the file. With FenixPyre, every file has its own independent security perimeter, and every request to use it is verified.
Integrations
Seamless product integrations with a wide array of data repositories and DLP products reduces complexities and friction while maximizing your return on your investments.












Frequently Asked Questions
Frequently Asked Questions
Frequently Asked Questions
What are the key components of a file-centric security platform?
What are the key components of a file-centric security platform?
What are the key components of a file-centric security platform?
What are the benefits of using a file-centric security platform for cloud environments?
What are the benefits of using a file-centric security platform for cloud environments?
What are the benefits of using a file-centric security platform for cloud environments?
How file-centric security platforms help meet compliance mandates like CMMC and HIPAA?
How file-centric security platforms help meet compliance mandates like CMMC and HIPAA?
How file-centric security platforms help meet compliance mandates like CMMC and HIPAA?
What role does data loss prevention play in file-centric security?
What role does data loss prevention play in file-centric security?
What role does data loss prevention play in file-centric security?
What is the importance of encryption in a file-centric security platform?
What is the importance of encryption in a file-centric security platform?
What is the importance of encryption in a file-centric security platform?
What are the main challenges in implementing a file-centric security platform?
What are the main challenges in implementing a file-centric security platform?
What are the main challenges in implementing a file-centric security platform?
What are the trade-offs between compression and encryption for file-centric security?
What are the trade-offs between compression and encryption for file-centric security?
What are the trade-offs between compression and encryption for file-centric security?

solutions

© 2018-2025 FenixPyre Inc, All rights reserved

solutions
7775 Walton Parkway
Suite 224
New Albany, OH 43054

© 2018-2025 FenixPyre Inc, All rights reserved

solutions
7775 Walton Parkway
Suite 224
New Albany, OH 43054

© 2018-2025 FenixPyre Inc, All rights reserved